Achieving a SOC 2 report completes a rigorous process that evaluates a company’s commitment to protecting customer data and maintaining strong internal controls. For many organizations, it’s among the first milestones in building a trustworthy security posture, and SOC provides a valuable pathway to other widely accepted standards and frameworks including HITRUST e1.
The HITRUST e1 certification, increasingly requested by large customers, offers a prescriptive, validated tool for strengthening your security efforts. The certification, while newer than SOC 2, is gaining traction among organizations seeking deeper security assurance or operating in regulated environments.
As a result, more companies are using SOC 2 as a foundation and layering HITRUST e1 for enhanced credibility and security (especially in industries where security expectations are strict).
For companies that have a SOC 2 report, the considerable overlap between the two frameworks means much of the groundwork is already done
SOC 2 vs. HITRUST e1: What’s the Difference?
While both frameworks address organizational security, SOC 2 and HITRUST e1 take different approaches to providing assurance.
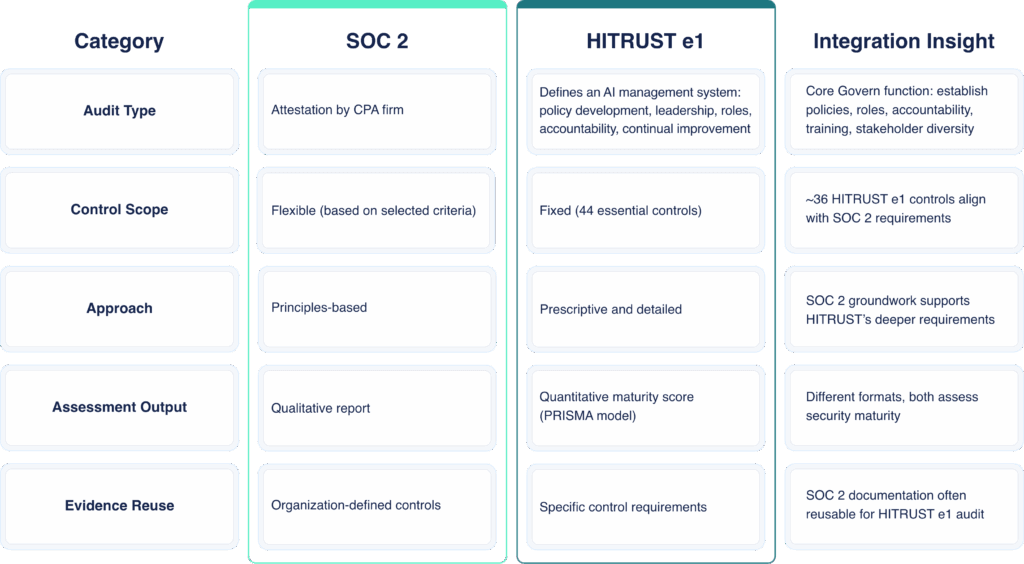
A SOC 2 report is an attestation issued by a public accounting firm that evaluates how well your organization’s controls align with Trust Services Criteria developed by the AICPA. A SOC 2 report, based on the auditor’s opinion, is not a formal certification.
In contrast, HITRUST e1 is a certification developed by the HITRUST organization validating that an organization meets a specific set of 44 foundational controls. A HITRUST audit is performed by an authorized External Assessor, which sends the results of its assessment (including testing controls, evidence, and maturity level scores) to HITRUST for review. The final certification decision is made by HITRUST.
Another key difference is how each framework approaches audit scoping. SOC 2’s scope is defined by the Trust Services Criteria you choose. The Security criterion is required, and organizations have the option to add Availability, Confidentiality, and others. The appropriate controls are reviewed by your auditor.
HITRUST e1 has a fixed scope: 44 essential controls that apply across the board. That consistency makes it easier to compare assessments and benchmark progress.
Beyond the fixed HITRUST e1 requirements, organizations have the option to scope in controls from other authoritative frameworks such as HIPAA, NIST, or others.
Similarly, SOC 2 outlines what needs to be protected but lets the organization decide how to accomplish that. HITRUST e1 is prescriptive, spelling out the framework’s requirements for each control.
For example, while SOC 2 might require that backups exist, HITRUST e1 could specify that backups must be stored offline in an immutable format. That level of detail pushes organizations toward a more consistent and robust security posture.
The results also look different. The SOC 2 process results in a qualitative report that reflects the auditor’s assessment. HITRUST e1 uses a quantitative scoring system based on the HITRUST CSF PRISMA maturity model. That score gives you a measurable view of your security maturity.
Why HITRUST e1 Is Worth It
Beyond the operational efficiencies, HITRUST e1 offers strategic benefits in several areas.

HITRUST can boost market trust because the certification is widely recognized and signals a mature security posture. HITRUST was developed to meet the security and regulatory requirements of the healthcare sector. More recently, it’s being adopted extensively among technology and SaaS providers, business services firms, and financial services companies.
HITRUST sets the stage for future growth, with HITRUST e1 offering an entry point to a broader certification ecosystem. The work done to obtain e1 certification provides a foundation for more advanced certifications like HITRUST i1 or r2, which may become relevant as your business scales or enters new markets.
HITRUST in general also strengthens your security. Its prescriptive nature requires a deep examination of your controls, helping to identify potential issues that might be missed in a more flexible framework.
HITRUST also incorporates threat-informed validation. Using the MITRE ATT&CK framework, it tests whether your controls (such as access management, endpoint protection, and patching) reduce the risk of known attacker behaviors.
From SOC 2 to HITRUST e1: A Clear Compliance Path
If you’ve already completed a SOC 2 audit recently, your organization has a head start on a HITRUST e1 assessment. Much of the evidence and documentation collected for SOC 2 can be reused for HITRUST e1. Overall, about 36 of the 44 HITRUST e1 controls align with SOC 2 requirements.
The next step is mapping your SOC 2 controls to the HITRUST e1 framework to identify where you’re already covered and where gaps exist between the two frameworks.
At this stage, a readiness assessment can be an effective way to identify potential issues that could preclude final certification. Resolving those gaps before submitting audit results for HITRUST review can make the process smoother and reduce the risk of failing the assessment.
During your preparation, leveraging a GRC (governance, risk, and compliance) platform can streamline the process of mapping evidence from a SOC 2 audit into a HITRUST e1 assessment. These platforms provide centralized documentation, automated control mapping, and workflow capabilities that reduce manual effort and improve traceability between frameworks.
Since SOC 2 and HITRUST share overlapping control requirements (particularly around data protection, access management, and incident response) a GRC tool can help identify reusable artifacts and align them with HITRUST’s specific criteria.
While this approach can accelerate readiness and reduce redundancy, it’s important to note it does not guarantee successful HITRUST certification. Each framework has unique requirements and validation standards, so organizations must ensure full compliance by completing a thorough gap analysis and remediation.
There’s value in working with a CPA firm experienced with SOC 2 that is also a HITRUST Authorized External Assessor. That dual capability can streamline the process, reduce costs, audit fatigue and ensure consistency across both evaluations.
Some organizations choose to conduct SOC 2 and HITRUST e1 assessments simultaneously. Others follow up HITRUST immediately (within about six months) after SOC 2. With either approach, the overlap in evidence collection can save time and effort.

HITRUST Offers a Strategic Next Step
SOC 2 is a strong start, and HITRUST e1 builds on that momentum by offering a clear, validated path to a mature and credible security posture. For organizations serious about protecting data and earning trust, it’s a step worth considering.
To learn more about how SOC 2 and HITRUST e1 work together, and how SOC 2 can provide a compelling pathway to HITRUST certifications, contact us.
















