In today’s threat landscape, proactive security testing is essential for protecting sensitive data and maintaining regulatory compliance. Frameworks like SOC 2, ISO/IEC 27001, and HITRUST require organizations to demonstrate their systems can withstand potential attacks.
But when it comes to testing your defenses, one size doesn’t fit all.
Penetration testing and red team exercises simulate real-world attacks, but they serve different purposes and require different levels of security maturity. How do you know which is right for your business?
Understanding these methods can help you make informed decisions about your security investments and protect your business more effectively from evolving cyber threats.
What Is Penetration Testing?
Penetration testing, often called “pen testing,” is a controlled simulation of a cyberattack designed to uncover vulnerabilities in your systems, applications, or networks. A pen test is usually conducted over a set period and targets specific assets, such as your external web applications, internal infrastructure, or cloud environments.
Examples might include testing a customer portal for SQL injection flaws, probing internal systems for segmentation gaps, or evaluating misconfigured access privileges.
Think of a pen test as a targeted security check-up with clear boundaries and objectives, making them practical for organizations with defined security concerns. Pen tests may be conducted with varying degrees of knowledge about your environment, ranging from “white box” (full access and visibility) to “gray box” (limited knowledge).
Common goals of penetration testing include:
- Discovering and fixing vulnerabilities before attackers do.
- Meeting compliance requirements from regulators or customers.
- Testing the effectiveness of security controls, patches, and configurations.
Typical engagement durations range from a few days to a couple of weeks, providing actionable results within a reasonable timeframe.
What Is a Red Team Exercise?
A red team exercise takes security testing to another level by conducting a full-scope, goal-oriented simulation that mirrors real-world cyberattacks. Unlike penetration testing, red teaming employs the tactics, techniques, and procedures used by threat actors to create a realistic adversarial scenario.
The aim isn’t just to find weaknesses, but to discover how far an attacker can go without being detected.
Unlike traditional pen tests, red team operations are stealthy and persistent. They unfold over several weeks or even months, often without alerting your defenders. These exercises test your organization’s detection capabilities, incident response procedures, and overall security resilience.
Red teams use a wide range of attack vectors: phishing emails, social engineering, privilege escalation, and even physical entry. A successful red team exercise might end when the attacker gains domain admin access, exfiltrates sensitive data, or bypasses all security layers to reach a protected business asset.
Red-team assessments are ideal for evaluating how well your security team detects, responds to, and recovers from real-world attack scenarios. But they require a mature cybersecurity program and a willingness to expose gaps in detection and response capabilities.
Key Differences: Pen Testing vs. Red Teaming
| Penetration Testing | Red Team Exercise |
| Finds and exploits vulnerabilities | Tests detection, response, and business impact |
| Scoped and time-boxed | Broad, goal-driven, long-term |
| Often known to defenders | Kept secret from defenders |
| Evaluates systems and configurations | Evaluates people, processes, and technology |
| Supports compliance requirements | Supports advanced threat simulation and readiness |
Which Is Right for Your Organization?
Companies must align their security testing approach with their business needs, regulatory requirements, cybersecurity maturity, and incident response capabilities.
Penetration testing offers a strong starting point if:
- You’re early in your cybersecurity journey.
- You need to meet compliance or client expectations.
- You want a fast, focused assessment of technical vulnerabilities.
Red team exercises may be more appropriate if:
- Your organization has mature detection and response capabilities.
- You’re looking to simulate complex, real-world adversary behavior.
- You want to measure the effectiveness of your entire security program.
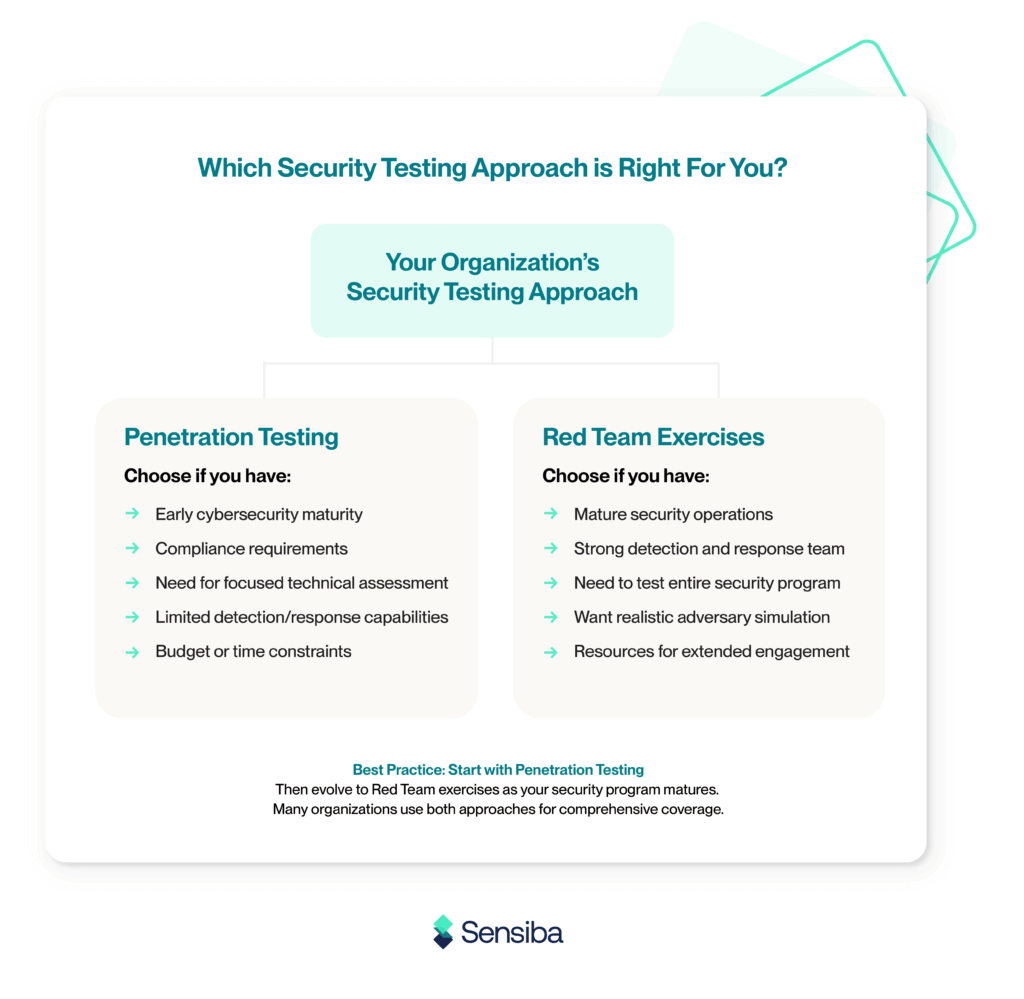
These approaches aren’t mutually exclusive. Many companies begin with regular penetration testing and introduce red teaming as their security programs mature. Layering both techniques provides a broader picture of your defenses, from identifying weak spots to understanding how your team responds under the pressure of an attack.
It’s important to remember security testing isn’t a one-time exercise, but an ongoing process that evolves with your business and the threat landscape. Penetration testing can provide a strong foundation by uncovering technical weaknesses and informing remediation efforts. Red team exercises build on that foundation by testing how well your organization responds when it matters.
If you’re unsure where to begin, a trusted cybersecurity partner can help assess your current maturity and guide your next steps. Whether you’re aiming for compliance or preparing for the unexpected, proactive security testing is an investment in resilience and your organization’s long-term success.
To learn more about pen testing and red-team exercises, contact us.
















