The HITRUST cybersecurity framework provides a comprehensive approach to managing data protection, information risk, and regulatory compliance.
First developed for the healthcare industry, HITRUST has been adopted by organizations in a variety of sectors. It offers a broad-ranging framework that integrates requirements from more than 40 global data security standards and regulations.
This blended approach can help organizations take a unified approach to addressing multiple compliance needs such as:
- The Health Insurance Portability and Accountability Act (HIPAA)
- The EU’s General Data Protection Regulation (GDPR)
- The California Consumer Privacy Act (CCPA)
- The Payment Card Industry Data Security Standard (PCI DSS)
Beyond compliance, HITRUST certification reduces the risk of data breaches by ensuring strong cybersecurity controls and demonstrates an organization’s commitment to data privacy that builds trust with clients and partners.
HITRUST certification is pursued most often by service providers, business partners, and vendors. HITRUST provides assurance to stakeholders that ththe organization has robust controls, policies, and procedures in place to process, store, and manage sensitive data responsibly.
Understanding HITRUST
HITRUST, originally an acronym for Health Information Trust Alliance, is designed to provide a standardized approach to managing data protection, information risk, and regulatory compliance.
The HITRUST organization is a privately held company. It provides the HITRUST CSF (Common Security Framework) and other tools for managing information risk and compliance. The organization collaborates with public and private sector experts to identify emerging cybersecurity threats and develop effective countermeasures.
19 Domains That Comprises the CSF
The HITRUST CSF encompasses a range of security controls organized into 19 high-level domains covering various aspects of information security. Each domain contains control specifications that organizations must implement to achieve compliance.

The framework also includes five levels of maturity that are aligned with a given organization’s risk factors: Policy, Procedure, Implementation, Measured, and Managed. Organizations need to complete the first three to obtain certification. The “Measured” and “Management” levels are optional, but can increase an organization’s certification score and demonstrate a stronger commitment to the framework’s goals.
This risk-based approach helps organizations align their security and compliance efforts with their exposures, and potentially offers a more cost-effective approach to cybersecurity by enabling organizations to customize their efforts for their specific needs.
The Benefits of HITRUST Certification
Achieving HITRUST certification offers numerous benefits:
- A Unified Compliance Approach: HITRUST harmonizes multiple regulatory requirements, including HIPAA, SOC 2, GDPR, PCI-DSS, and others. In addition to simplifying the overall compliance process for organizations, being able to demonstrate HITRUST certification may satisfy customer inquiries about compliance with other standards.
- Risk Mitigation: By meeting the requirements within the HITRUST standards, organizations can effectively identify and mitigate risks associated with handling sensitive information.
- Enhanced Trust: HITRUST certification demonstrates a commitment to high information security and privacy standards that builds trust among customers, partners, and other stakeholders.
- Marketplace Advantages: Organizations that achieve HITRUST certification may enjoy competitive advantages as prospects evaluate potential service providers.
The HITRUST Certification Process
Obtaining compliance certification from a HITRUST Authorized External Assessor involves a process that, depending on an organization’s size, complexity, risk factors, and readiness, can take between three to 18 months to complete.
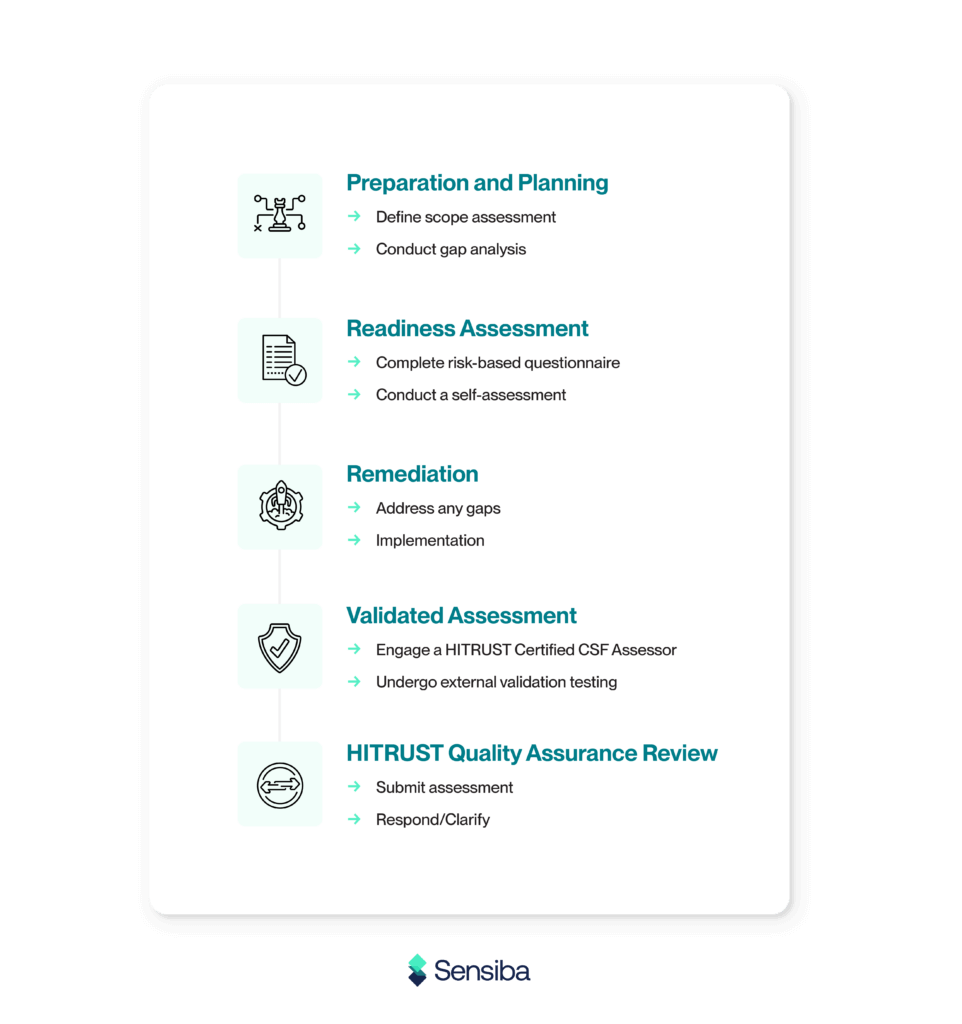
There are several steps for most organizations:
- Preparation and Planning
- Define the scope of the assessment, including systems, processes, and data.
- Conduct a gap analysis comparing current security practices to the HITRUST requirements.
- Readiness Assessment
- Complete a risk-based scoping questionnaire to determine the controls to implement and the scope of the assessment.
- Conduct a self-assessment or readiness assessment.
- Remediation
- Address any gaps identified during the readiness assessment.
- Implement or update controls, policies, and procedures to align with HITRUST CSF requirements.
- Validated Assessment
- Engage a HITRUST Certified CSF Assessor to perform the validated assessment.
- Undergo external validation testing, which includes evidence reviews and possible on-site testing.
- HITRUST Quality Assurance Review
- Submit the completed assessment to HITRUST, which performs a quality assurance review.
- Respond to any additional requests for documentation or clarification.
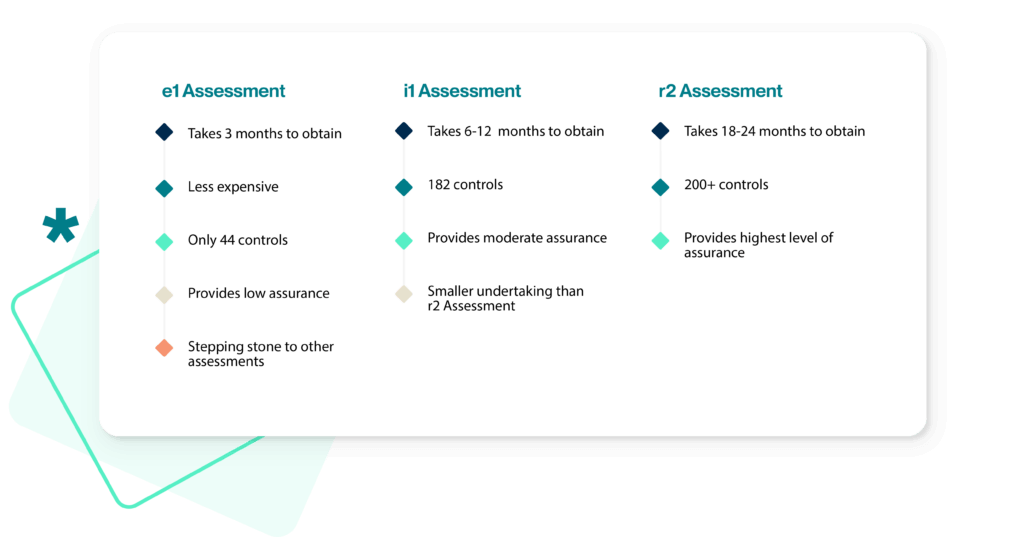
Based on the assessment results and quality assurance review, HITRUST will make the final decision for approving or denying the certification. If approved, HITRUST will issue a Certification that is valid for two years (r2) or one year (e1 & i1).
While the process can seem complex, HITRUST certification can help organizations enhance and streamline their overall cybersecurity and compliance while providing other compelling benefits. To learn more about HITRUST certification, contact us.
















