Table of Contents:
As a young consultant joining the assurance space, I was looking for opportunities to work in emerging technologies. Candidly, I just wanted to work on ‘cool’ clients, and those in the emerging tech space seemed to foot the bill. A fortunate conversation with a partner at my firm turned into a long discussion about blockchain and cryptocurrencies.
This was around 2019, and I had a faint understanding of crypto that was limited to knowing that Bitcoin existed, and that a guy I knew in high school had somehow made enough money to buy himself a brand-new BMW M3.
He tried to convince me to buy some, but it sounded like a scam. When he totaled that BMW and was promptly able to purchase a new one, I figured it had to be a scam because no high schoolers made that kind of money authentically.
The conversation with this partner, however, offered a change of tune that made me realize not only was this high schooler on to something in 2012, but that I probably missed out on making a fortune. This partner is an incredibly intelligent person whom I looked up to, who taught me about the underlying tech and its potential to completely change entire industries.
I figured if he believed in it that much, there must be something to it I didn’t understand. But I knew I wanted to learn.
What Is Blockchain?
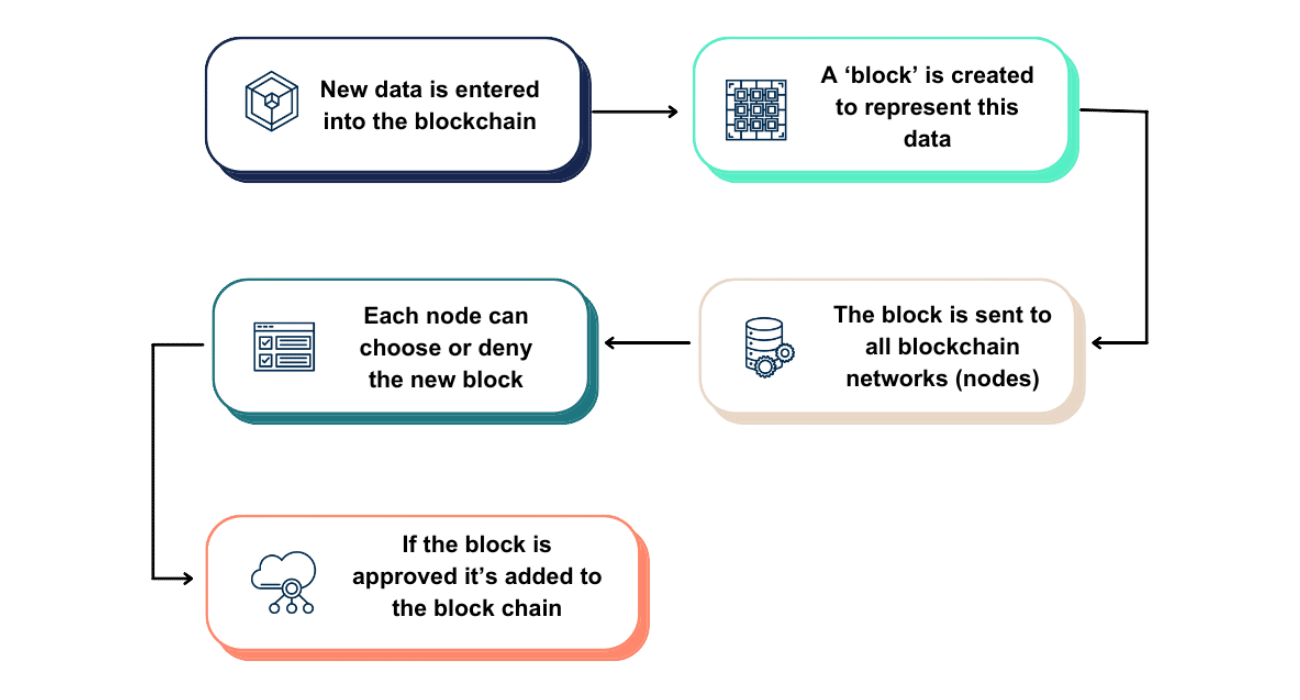
Blockchain is defined as a shared, immutable ledger that facilitates the process of recording transactions and tracking assets in a business network. All participants on the network using the shared database are referred to as nodes connected to the blockchain, with each maintaining an identical copy of the ledger. When one participant wants to transact with another, all nodes must use the pre-determined consensus mechanism to validate that transaction.
Upon validation, all copies of the ledger are updated with the new transaction information (i.e., a new block is added to the chain). These transactions, or blocks of transactions, cannot be deleted or altered. In the event of an alteration, the rest of the network would reject the alteration and exclude it from the blockchain.
Who Are the Key Players?
You can categorize key players into the following groups: Digital Asset Wallet Providers, Digital Asset Exchanges, Digital Asset Custodians, Cryptocurrency Payment Companies, and Utility Tokens.
These service providers need to be able to prove to customers that their platforms are secure. Some questions that a user entity of these service providers should ask are:
- How are digital assets going to be secured?
- How will the service provider prevent misappropriation of assets?
- What controls does the service provider have in place to reconcile customer balances to protect blockchain data?
- Does the service provider charge a fee to process transactions? If so, how are they ensuring the fee amount is agreed to by the customer?
- What controls does the service provider have in place to reconcile customer balances to protect blockchain data?
These groups and the organizations within them serve a mosaic of use cases ranging from supply chain tracking, financial transaction management, identity management, and much more. With the relatively nascent nature of the technology and lack of regulation in the industry, the need for comprehensive and scalable risk assessment frameworks is imperative.
How Does Third-Party Assurance Tackle This New and Complex Technology?
As the volume of entities and enterprises entering this space grows, the need for assurance in their use of the technology amplifies. These entities need to be aware of the risks involved and how to mitigate them appropriately.
In recent years, scandals have rocked the world of blockchain and digital assets, with “rug-pulls” becoming a known term. These scams, where developers or creators withdraw all funds or liquidity and disappear, raise significant concerns about the availability of services and access to funds for customers.
This is where Third-Party Assurance can step up. SOC 2, for example, provides critical assurance for blockchain systems by establishing rigorous security controls, third-party validation, and continuous compliance monitoring tailored to decentralized environments.
A SOC 2 report can provide assurance against traditional and blockchain-specific risks at a service provider. This is achieved by evaluating their controls over Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Other examples include:
- Immutable compliance evidence (such as automating evidence collection for access controls, security patches, incident responses, and other factors)
- Third-party risk mitigation, such as vendor compliance with appropriate security standards
- Regulatory alignment, including compliance with GDPR, CCPA, and financial regulations through documented data handling practices.
Key Blockchain and Digital Asset Terminology
Distributed Ledger Technology (DLT): A distributed, decentralized ledger technology that records transactions across a network of computers. Each transaction is grouped in a block and linked chronologically in a chain.
Block: A collection of transaction data.
Chain: A linked sequence of blocks, each referencing the previous one via a cryptographic hash.
Hashing: A cryptographic function that converts input data into a fixed-length string.
Nodes: Individual computers in the blockchain network that store copies of the ledger and follow the protocol.
Smart Contracts: Self-executing contracts with terms directly embedded into their code that execute actions automatically when predefined conditions are met.
Tokens and Digital Assets:
- Cryptocurrency: Digital currency native to a blockchain (e.g., Bitcoin and Ether)
- Utility Tokens: Provide access to a service or product.
- Security Tokens: Represent ownership in an asset, subject to securities regulation.
- Non-Fungible Tokens (NFTs): Unique digital assets verified on chain.
Public Blockchain: Open, permissionless networks (e.g., Bitcoin, Ethereum)
Private Blockchain: Permissioned networks with restricted access (e.g., Hyperledger Fabric)
Consensus Mechanisms: Protocols used by blockchain networks to agree on the validity of transactions and maintain the integrity of the distributed ledger.
- Proof-of-Work (PoW): Requires computational work to validate transactions (e.g. Bitcoin). PoW is very secure, but because of the mathematical computations required, it can be energy intensive.
- Proof-of-Stake (PoS): Validators for each block are chosen based on the number of coins they stake. This is a faster and more energy-efficient alternative to PoW. However, there is a risk of centralization due to wealthier users having more control of the network.
- Delegated Proof of Stake (DPoS): Stakeholders vote for a small number of delegates who validate transactions. This consensus mechanism allows for high throughput, but can pose a risk of cartel-like power behavior.
- Proof of Authority (PoA): Allows for a few trusted nodes to validate transactions based on reputation or permission. This is arguably the fastest and most efficient type of consensus mechanism, but also the least transparent. This is why it is usually most commonly seen on private blockchains.
- Practical Byzantine Fault Tolerance (PBFT): Nodes reach consensus through majority agreement despite possible malicious actors. This allows for high security and speed in small networks, but is not scalable for large public networks.
When I stepped into this space, I knew it would be a wild ride. Between the ever-changing regulatory landscape, emerging use cases beyond anything I could have conceptualized, and the volatile nature of the industry, the ride has been much like the technology itself: complex.
The see-saw can be balanced with the right expertise and assurance, allowing the pioneers to focus on innovating.
To learn more about applying the benefits of blockchain assurance, contact us.
















