With over 22,000 ISO standards in existence, it’s easy to feel overwhelmed by the alphanumeric combinations. However, for organizations focused on cybersecurity, privacy, and responsible AI, just a handful of ISO standards truly matter. Here’s a simplified look at the key frameworks and how they build on one another.
Putting the Information Security (IS) in ISO
At Sensiba, we focus on the following information security-related ISO Standards:
- ISO/IEC 27001: Information Security Management System
- ISO/IEC 27017: Information Security Controls (based on ISO/IEC 27001 for Cloud Services)
- ISO/IEC 27018: Code of Practice for Protection of Personally Identifiable Information (PII) in Public Clouds acting as PII Processors
- ISO/IEC 27701: Privacy Information Management System (PIMS)
- ISO/IEC 42001: Artificial Intelligence Management System
Why an ISO Suburb?
Traditionally, ISO standards are hard to digest. We’ve found the best way to break them down is to consider each standard as its own house that you can extend, subdivide, or build next to. Some standards listed above can be considered stand-alone homes, while others are extensions of existing homes.
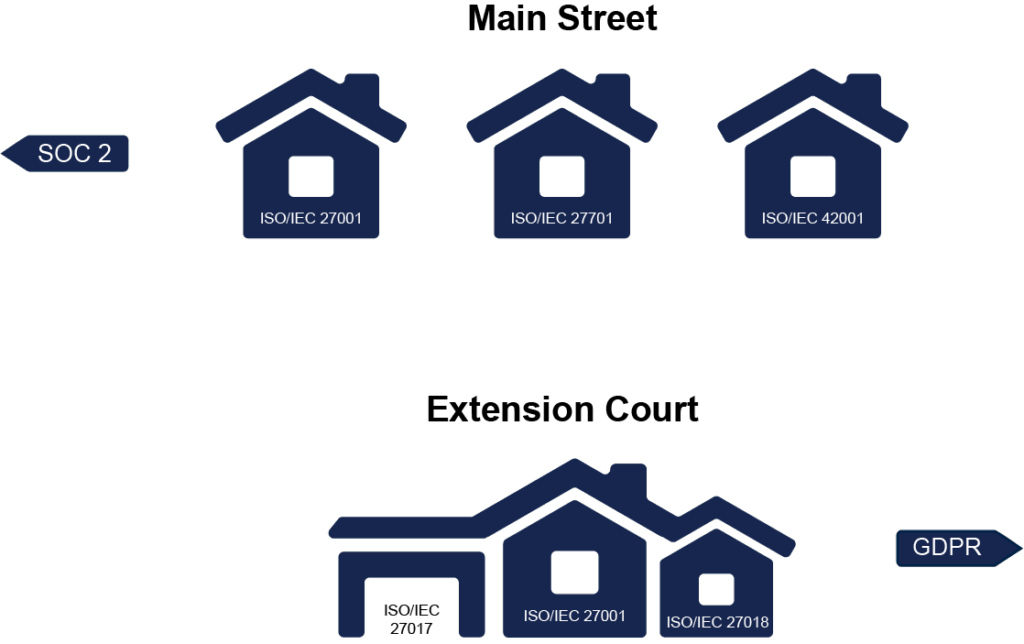
Let’s take a look around each house!
ISO/IEC 27001
General Overview:
- Considered one of the most recognized Information Security Standards globally.
- Consists of criteria (Main Requirements) and a list of common information security controls (Annex A) that exist to guide your organization in implementing an Information Security Management System (ISMS) and mitigating common information security risks.
Compliance:
- Implement all Main Requirements.
- Determine which of the Annex A controls apply to your organization (e.g., controls required to mitigate identified risks).
- Don’t set it and forget it, rinse and repeat! Your ISMS is now a living, breathing household you worked hard to build; maintain it to ensure you reap the benefits.
What if my house has an existing framework (e.g., SOC 2)? Can I still build an ISMS?
- You sure can, and you can utilize some of the existing framework!
- The ISO/IEC 27001 criteria are more rigid than you may have experienced with SOC 2, but with a bit of refurbishment, they will all work in unison!
- The Annex A controls, and typical SOC 2 controls are like Scandinavian design and minimalism–a match made in heaven!
Does my house need ISO/IEC 27017 and ISO/IEC 27018? If so, what will happen if I add them?
- Those standards are an additional set of Annex A controls pertaining to cloud service providers and/or cloud service providers who hold PII.
- Add the applicable ISO/IEC 27017 and/or 27018 controls to your existing ISO/IEC 27001 Annex A controls, and you’re done. Just like that, your ISO/IEC 27001 house has a new addition!
ISO 27701: Privacy Information Management System
General Overview:
- While it is an extension of ISO/IEC 27001, ISO/IEC 27701 has its own set of criteria to guide an organization in building and maintaining a Privacy Information Management System (PIMS).
Compliance:
- Implement all Main Requirements.
- Determine which of the Annex A controls apply to your organization (e.g., controls required to mitigate identified risks).
- Don’t set it and forget it; be sure to maintain your PIMS.
Does my PIMS have to be a standalone home, or can it be part of my ISMS?
- Consider it a duplex; there will be some adjoining walls (both sets of criteria have the same structure and flow). However, one is focused on Information Security, and the other on Privacy Information, so ensuring your processes cover both clearly is vital. The last thing you want to do is combine them and have one fall by the wayside.
PIMS, GDPR, HIPAA… A lot of letters, can any of them be mashed together?
- In essence, privacy controls are privacy controls. If you were to do a multi-standard audit with Sensiba, you would find plenty of overlap across the SOC 2 Privacy Trust Service Criteria, HIPAA, GDPR, CCPA, and ISO/IEC 27701, as well as similar expectations within policies, procedures, and activities.
- Many of these frameworks share foundational privacy principles, such as data minimization, access controls, incident response, and user consent, that mean a single control or policy can often fulfill requirements across multiple standards.
ISO/IEC 42001: AI Management System
General Overview:
- The new kid on the block. The architects looked at your brick houses or your concrete houses and decided to bring along a 3D printer and print out a brand-new AI-generated house.
- It provides a structured framework for organizations to manage the risks and responsibilities associated with developing, deploying, or using AI systems.
- Criteria and controls are designed to create a management system for the use of AI.
Compliance:
- Implement all Main Requirements.
- Determine which of the Annex A controls are applicable for your organization (e.g., controls required to mitigate identified risks).
- Don’t set it and forget it, rinse and repeat!
Does my AI Management System have to be a standalone home, or can it be part of my ISMS?
- As before with ISO 27701 and PIMS, consider it a duplex, with one half focused on Information Security and the other on the use of AI.
So…. How Do These Audits Actually Work?
Like any new build, getting started can often be confusing. That is why we are here to help navigate your journey. If you’re ready to start building your ISO dream home, contact us today.
















